Outbound Attack Interception
Outbound Attack Defense, efficiently prevents malicious remote control and Botnet threats away from your computer, and defenses computer operating system and network resource from malicious occupancy.
Launch Rising Personal Firewall program main interface and, click [Settings] -> [Net Defence] -> [Outbound Attack Interception] to configure and manage rules of outbound attack interception.
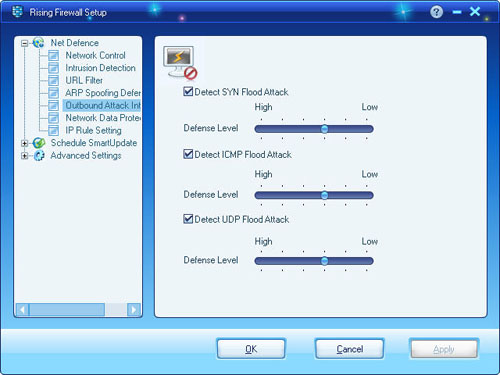
Within Outbound Attack Defense, Rising Personal Firewall efficiently detects outbound SYN, ICMP, and UDP files. Within window of Outbound Attack Interception, computer users can configure Internet protocol packet types, and click button of [OK] to save changes.
Three Optional Detections:
- Detecting SYN Flood Attack
- Detecting ICMP Flood Attacks
- Detecting UDP Flood Attacks
As to each detection contents, computer users can customize [Outbound Attack Interception] according to preferred sensitivity. Meanwhile, Rising Personal Firewall preset “Medium” as default interception sensitivity trigger; so while computer users customize sensitivity trigger as “High”, interception shall be executed in case of high outbound attack traffic; and while computer users customize sensitivity trigger as “Low”, interception shall be executed in case of a lower outbound attack traffic. This suggests that High level detection requires huge amount of outbound attack traffic; in the other hand, lower interception efficiency always goes with lower security sensitivity.
| prev ARP Spoofing Defense | next NetWork Data Protection |