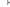IP Rule Setting
Rising Internet Security 2011 filters IP packets based on customized IP rules.
Launch Rising Internet Security 2011 program main interface and, click [Settings] -> [Net Defence] -> [IP Rule setting] to configure and mange rules of IP packets filter.
Notice: More IP rules shall slow down Rising Internet Security 2011 performance; so computer users do not need add IP rules assigned with applications, because Windows shall enable ports while in need. Meanwhile, there is no need of adding defensive IP rules for concerned built-in IP rules can update automatically.
Add IP Rules
Click button of [Add] or select [Add] on context menu and, launch [IP Rules Settings] window; then enter name of rules, applied type, and how to handle IP packet which triggered this customized IP rules. Then, click button of [Next] to enter address of local computer and remote computer in communication. And then, click button of [Next] to proceed, and select protocol and port number, appoint content character or ICP flag, as well as whether configure appoint content character or not, etc. Click button of [Next] to proceed, and select caution measure while customized IP rules get triggered, and then click [OK] to save changes.
Notice: Appointed protocol number goes from 0 to 255.
Finally, select optional caution measure from Tray Animation, Prompt Balloon, Prompt Window, Noise Alarm and Logs.
Edit IP Rules
Select highlighted IP rules to be changed and, click [Edit] to launch window of [IP Rules Setting], and then change corresponding options. For approach, please refer to "Add IP Rules” for details.
Delete IP Rules
Select highlighted IP rules to be deleted and, click button of [Delete]; then selected IP rules shall be deleted after confirmation.
Notice: While delete IP rules, computer users can take multiple selections combined with [Ctrl] or [Shift] key.
Import IP Rules
Click button of [Import] and, select existing IP rules file (with extension of .fwr) on popup file selecting window, and then click button of [Open] to proceed. If there were IP rules already existed,Rising Internet Security 2011 shall ask computer users whether delete existing IP rules, or not; if computer users select [Yes], then the existing IP rules shall be deleted and new IP rules shall be imported; if [No], existing and the newly imported IP rules shall be both saved.
Export IP Rules
Click button of [Export] and, enter file name on popup window, and then click button of [Save] to accomplish IP rules export operation.
Default
Click button of [Default] to erase all customized IP rules to default settings.
Trusted Zone Settings
Click button of [Settings] on the right part of [Trusted Zone] and, configure trusted zone in popup window. Trusted Zone is generally applied to LAN environment. Computer users can add trusted users/devices in LAN into local Trusted Zone to avoid inconvenient operations from Rising Internet Security 2011.
Notice: Computer security inversely proportional against workability. In another word, high operational performance (great convenient workability) always goes with low computer security performance. Therefore, adding trusted users/devices in LAN to Trusted Zone suggests that computer users have great faith in security status of these computers; so, Rising Internet Security 2011 will not filter any IP packet from those devices, even packets of malicious virus program.
Black/White List Settings
Click button of [Settings] of [Black/White List] and, configure Black List or White List of IP address on popup window through operations of Add, Delete, Edit, Import or Export IP rules. Black/White List option supports specific IP address and scale selections settings. Computers whose address assigned to Black List can not communicate with local computer with security protection from Rising Internet Security 2011; meanwhile, computers whose address assigned to White List can communicate with local computer with security permission.
Port Rules
Click button of [Settings] right allocated at [Port Rules] and, configure port rules on popup window through operations of Add, Edit, Delete, Import or Export port rules. Port Rule option supports specific Port number and port list, protocol type of TCP, UDP or both; as well as Allow or Deny as approach behavior.
| prev Intrusion Detection | next Network Defence |